Blockchain security experts have uncovered a malicious mobile application, BOM, responsible for stealing over $1.82 million in cryptocurrency. According to blockchain security firms SlowMist and OKX Web3 Security, the app secretly accessed users' private keys and mnemonic phrases.
区块链安全专家发现了一个恶意移动应用程序BOM,负责窃取超过182万美元的加密货币。 根据区块链安全公司的说法,该应用程序秘密访问了用户的私钥和助记符。
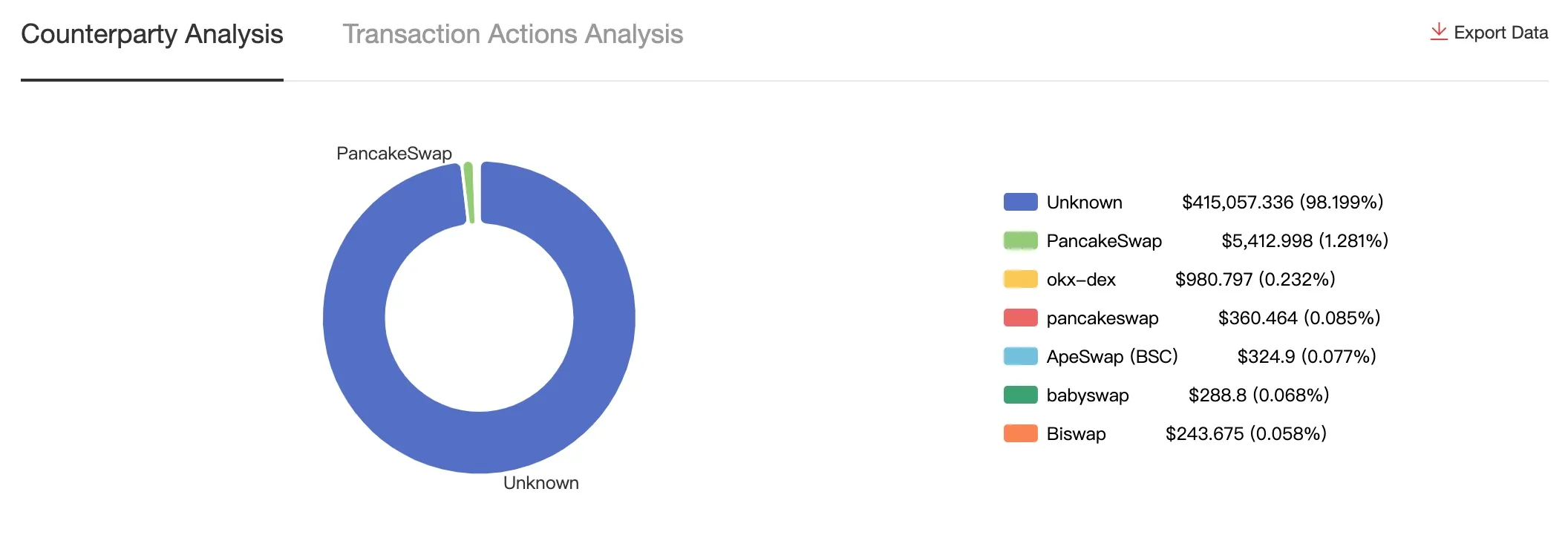
Analysis of stolen funds movement from the BOM creator across multiple DEXs | Source: SlowMist
分析来自多个DEX的BOM创建者的偷资金运动|资料来源:慢速派
SlowMist's February 27th report detailed the first unauthorized transactions occurring on February 14th. On-chain analysis revealed BOM as a fraudulent app that tricked users into granting excessive file access permissions. Once granted, the app scanned the device, exfiltrated wallet data, and transmitted it to a remote server.
Slowmist的2月27日报告详细介绍了2月14日进行的首次未经授权的交易。 链分析显示BOM是一个欺诈性应用程序,它欺骗用户授予过多的文件访问权限。 批准后,该应用程序扫描了设备,删除钱包数据,然后将其传输到远程服务器。
The app's request for unnecessary permissions, such as access to photos and media, was flagged as highly suspicious. SlowMist noted, "On iOS, the app deceptively requests permissions, claiming this access is necessary for normal operation. This behavior is highly suspicious—a blockchain application has no legitimate reason to require access to the photo gallery."
该应用程序要求的不必要权限的请求(例如对照片和媒体的访问)被标记为高度可疑。 Slowmist指出:“在iOS上,该应用程序欺骗性请求权限,声称此访问是正常操作的必要条件。此行为高度可疑 - 区块链应用程序没有正当理由需要访问照相馆。”
SlowMist tracked the stolen funds across multiple blockchains, identifying at least 13,000 victims. The main hacker address (0x49aDd3E…) transferred funds through BNB Chain, Ethereum, Polygon, Arbitrum, and Coinbase's Base. Stolen cryptocurrencies included Tether (USDT), Ethereum (ETH), Wrapped Bitcoin (WBTC), and Dogecoin (DOGE).
Slowmist追踪了跨多个区块链中被盗的资金,确定了至少13,000名受害者。主黑客地址(0x49Add3e…)通过BNB链,以太坊,多边形,索赔和Coinbase的基础转移了资金。 被盗的加密货币包括Tether(USDT),以太坊(ETH),包裹的比特币(WBTC)和Dogecoin(Doge)。
While the perpetrators remain unidentified, SlowMist analysts observed the app's backend services were offline during their investigation, suggesting an attempt to conceal their activities. Some funds were laundered through decentralized exchanges like PancakeSwap and OKX-DEX.
虽然肇事者仍然身份不明,但慢慢分析师观察到该应用程序的后端服务在调查过程中脱机,这表明试图掩盖他们的活动。 一些资金通过分散的交易所(如Pancakeswap和Okx-Dex)洗钱。


 CoinsProbe
CoinsProbe Coin Edition
Coin Edition crypto.news
crypto.news DogeHome
DogeHome TheNewsCrypto
TheNewsCrypto COINTURK NEWS
COINTURK NEWS BH NEWS
BH NEWS crypto.news
crypto.news






















